This blog article is intended for Initial IT Managed Service clients only
What Is End-User Verification (and Why It Matters)?
End-User Verification is exactly what it sounds like, confirming that the person trying to access your system is who they say they are.
In the world of cybersecurity, it’s not enough to just have a password anymore. With threats becoming more sophisticated, we need smarter ways to verify identity. That’s where end-user verification steps in.
You’ll no doubt have seen the headlines, Marks & Spencer, The Co-op, Harrods all recently hit by cyber attacks. The truth is, many of these breaches could have been stopped in their tracks with a Zero Trust approach and proper identity checks.
Put simply, it's the process of confirming and validating a person’s identity before granting them access to systems, apps, or data.
The goal? To make sure only the right people get through your digital door, keeping out unauthorised users, accidental breaches, and malicious actors.
Whether it's a staff member logging into their email or a partner accessing shared files, end-user verification helps ensure your business stays secure, compliant, and one step ahead of cyber threats.

Why Does Initial IT Use End-User Verification?
Let’s be honest, trust is earned, not assumed. That’s why we operate with a Zero Trust Policy at Initial IT.
Zero Trust is a modern security approach based on a simple rule: never trust, always verify. It doesn’t matter where you’re working from, what device you’re using, or how often we’ve spoken, every access attempt has to prove its legitimacy. And that includes every call to our service desk.
Why Zero Trust Is Our Standard
We didn’t adopt Zero Trust because it sounds cool (although it kind of does). We did it because it’s essential in today’s threat landscape. Here’s why:
🔄 The Old Perimeter Is Gone
Back when everyone worked in the office and everything sat inside a firewall, security was simpler. Not anymore. Remote work, cloud apps, and mobile access mean threats can come from anywhere. Zero Trust recognises that the network perimeter is no longer a fence, it’s a revolving door.
🧠 Threats Are Smarter
Basic security just doesn’t cut it against today’s attackers. AI-driven voice phishing, deepfakes, and persistent threat actors demand layered, continuous protection. ZTP helps us respond faster and block attacks before they escalate.
🔐 Data Lives Everywhere
Sensitive data isn’t just stored in one place anymore. It's in your email, cloud storage, business apps, spread across multiple devices. We use Zero Trust to ensure only the right people can access the right data, from the right place.
📱 The Workforce Is Mobile
Your team might be working from home, the office, or a coffee shop. Zero Trust doesn't care where they are, it just makes sure they are who they say they are.
👀 Even Admins Don’t Get a Free Pass
Privileged access is a major target for attackers. With Zero Trust, even our most senior technicians must verify every time. That’s how we reduce the risk of credential misuse.
🕵️ Insider Threats Are Real
Most employees are trustworthy. But mistakes happen, and sometimes, so do bad intentions. ZTP enforces least-privilege access and continuous monitoring to limit potential damage.
✅ It Helps with Compliance
From GDPR to Cyber Essentials and beyond, Zero Trust helps meet strict data protection requirements and demonstrates that your business takes security seriously.
So How Do We Verify Identity?
Every call to our service desk includes a 30-second End-User Verification process. Yes, it’s short, but it’s powerful.
We use Multi-Factor Authentication (MFA) built on three key pillars:
1. Something You Know
Passwords, PINs, or answers to security questions
Often forgotten, sometimes weak, and occasionally shared, so not reliable on their own
2. Something You Have
Your phone or device (via call, SMS, or app push)
If you’ve got the device, you’re likely the real deal
3. Something You Are
Fingerprint, facial recognition, or other biometrics
Unique to you and hard to fake, especially when stored securely on your mobile
Why This Matters
🔒 Identity threats have increased by 144% since 2022, and they’re now the leading cause of security alerts and investigations, three years running.
(Source: Annual Threat Report 2024)
That’s why we treat identity verification as non-negotiable.
Whether you're calling for support or accessing business-critical systems, verification protects you, your data, and your business reputation.
Initial IT has the below methods available for verification
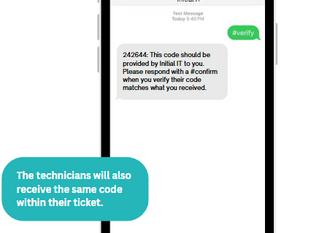
SMS Verification: Quick, Secure, and Easy
One of the simplest ways we verify your identity is via SMS verification.
🔒 How It Works
If we’ve got a valid mobile number on file for you, we’ll send a six-digit verification code by text message. This message will always come from a designated Initial IT number, so you’ll know it’s legit.
When prompted, just repeat the code back to your service desk technician, within the time window, and you're good to go.
It’s quick. It’s secure. And it helps keep your account protected from unauthorised access.

Microsoft Authenticator: One-Tap Approval
If you’ve already set up Microsoft Authenticator, verifying your identity is as easy as tapping your screen.
🔐 How It Works
When prompted by our team, just open the Microsoft Authenticator app on your mobile device and tap “Approve” to complete verification.
That’s it, no codes, no hassle. It’s fast, secure, and built right into your Microsoft 365 environment.

Email Verification: Straight to Your Inbox
Prefer to verify via email? No problem—as long as we’ve got a valid email address on file for you.
📧 How It Works
When a verification is triggered, you’ll receive an email from verify@initialit.co.uk.
Inside the email, there’ll be a secure link, simply click the link within the specified time window to confirm your identity.
It’s straightforward, secure, and gets you connected to our team without delay.

The final step is to click on “Validate”.

If the validation is completed successfully, you will see the following:

You Are Now Verified!
Thanks for completing the process, you're good to go.
Verifying your identity helps us keep your data safe, your business secure, and the bad guys out. Simple as that.
Need help or have questions? Just give us a shout, we’re here to make IT easy.
Keeping Your Details Up to Date Helps Us Help You Faster
At Initial IT, delivering top-tier service isn’t just our goal, it’s our standard. We know that clear communication is key to resolving your issues quickly and keeping your business running smoothly.
To support this, we’ll now be requesting your current phone number. This ensures our records are accurate and allows our technicians to assist you more efficiently, whether it’s for security verification or simply getting back to you with updates.
Thanks for helping us keep things seamless, secure, and stress-free.
Please follow the steps below
You will receive an email just like the one below. The email will come from

You have the option to opt in for SMS notifications and, if applicable, update your mobile number for SMS communications. This will ensure you receive timely updates and alerts regarding your service.

Click “Submit” to securely update your contact details in our system. Having your current phone number on file allows our technicians to:
Send support-related messages
Provide timely updates on your requests
Verify your identity quickly and securely during service interactions
This small step helps us streamline support, enhance your security, and improve your overall experience.
Thanks for helping us keep things efficient, secure, and running smoothly at Initial IT.